AWS Web Application Firewall

AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources. AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that filter out specific traffic patterns you define.
You can get started quickly using Managed Rules for AWS WAF, a pre-configured set of rules managed by AWS or AWS Marketplace Sellers. The Managed Rules for WAF address issues like the OWASP Top 10 security risks. These rules are regularly updated as new issues emerge. AWS WAF includes a full-featured API that you can use to automate the creation, deployment, and maintenance of security rules.
Web Traffic Filtering
AWS WAF lets you create rules to filter web traffic based on conditions that include IP addresses, HTTP headers and body, or custom URIs. This gives you an additional layer of protection from web attacks that attempt to exploit vulnerabilities in custom or third party web applications. In addition, AWS WAF makes it easy to create rules that block common web exploits like SQL injection and cross site scripting.
AWS WAF allows you to create a centralized set of rules that you can deploy across multiple websites. This means that in an environment with many websites and web applications you can create a single set of rules that you can reuse across applications rather than recreating that rule on every application you want to protect.
API and CDK
AWS WAF can be completely administered via APIs. This provides organizations with the ability to create and maintain rules automatically and incorporate them into the development and design process. For example, a developer who has detailed knowledge of the web application could create a security rule as part of the deployment process. This capability to incorporate security into your development process avoids the need for complex handoffs between application and security teams to make sure rules are kept up to date.
AWS WAF can also be deployed and provisioned automatically with AWS CloudFormation sample templates that allow you to describe all security rules you would like to deploy for your web applications delivered by Amazon CloudFront.
Real Time Visibility
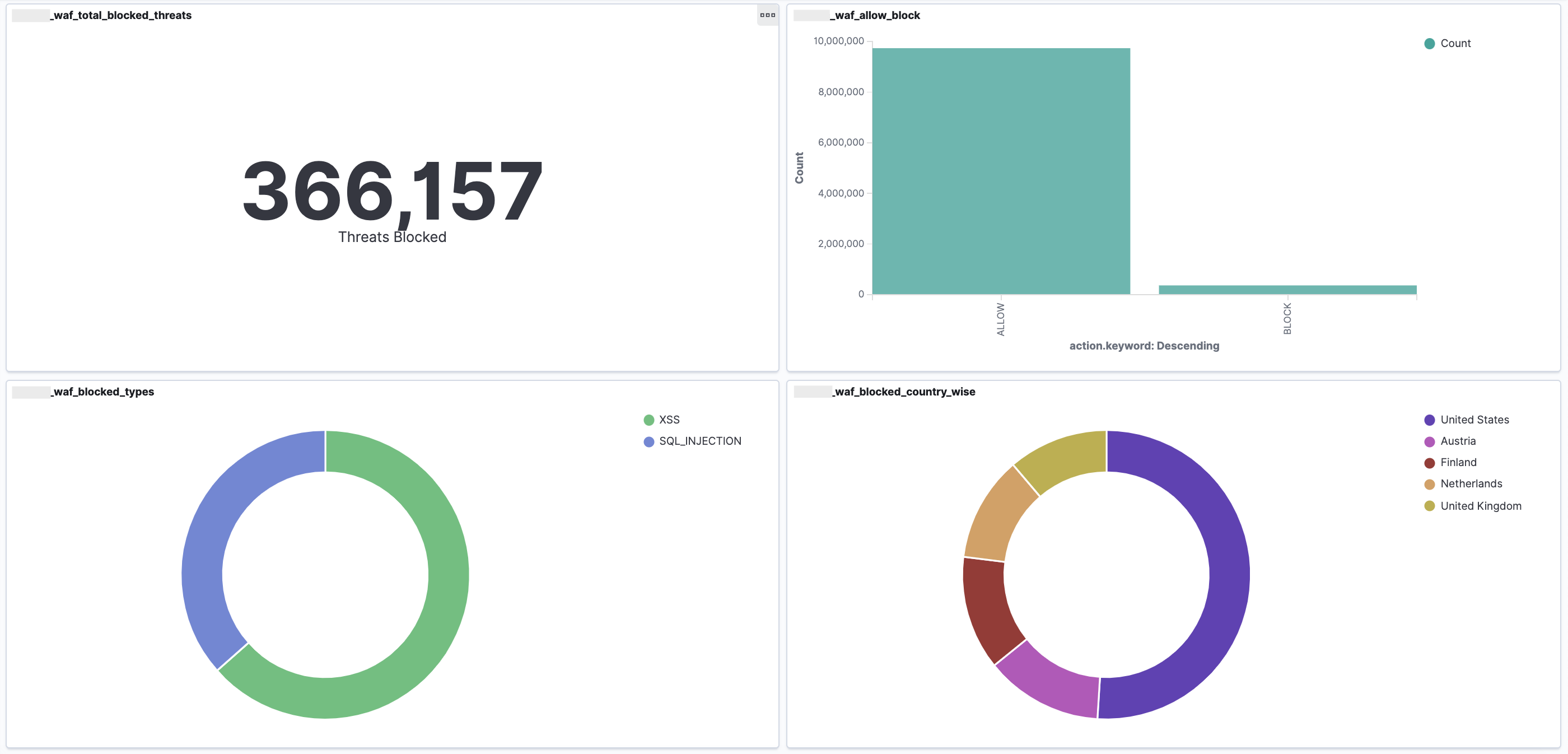
AWS WAF provides real-time metrics and captures raw requests that include details about IP addresses, geo locations, URIs, User-Agent and Referers. AWS WAF is fully integrated with Amazon CloudWatch, making it easy to setup custom alarms when thresholds are exceeded or particular attacks occur. This information provides valuable intelligence that can be used to create new rules to better protect applications.
Customized Dashboards and Reporting
WAF real time logs can be ingested into an ELK stack, with the time series data being stored in Elasticsearch and data can be visualized and dashboards created in Kibana or Grafana.